The global cybersecurity market is projected to grow from $173 billion to $270 billion by 2026, as the global threat landscape continues to evolve in terms of scale and sophistication. However, while new technologies offer hope to combat cyber threats more effectively, they themselves pose novel and more advanced threats.
Cyber Crimes Will Cost The Global Economy $6 Trillion
With the increased complexity and diversity of cyber threats, the impact of cyber attacks is growing substantially around the world.
Cybersecurity Ventures predicts that cyber crimes will cost the global economy $6 trillion annually by 2021, up from $3 trillion in 2015 and more than the global trade of all major illegal drugs combined. These costs include destruction and theft of personal and financial data, stolen money, lost productivity, theft of intellectual property, disruption of business activities, forensic investigation, restoration of hacked systems, and reputational damage.
Despite ongoing efforts to mitigate risks associated with cyber threats, all organizations remain vulnerable. As articulated by John Chambers, the former executive chairman and CEO of Cisco Systems:
There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked.
The Current Global Threat Landscape
The current global threat landscape is rapidly evolving. Although cyber threats have existed since the inception of the internet, the level of sophistication has grown exponentially in recent years with the rapid advancement in technology.
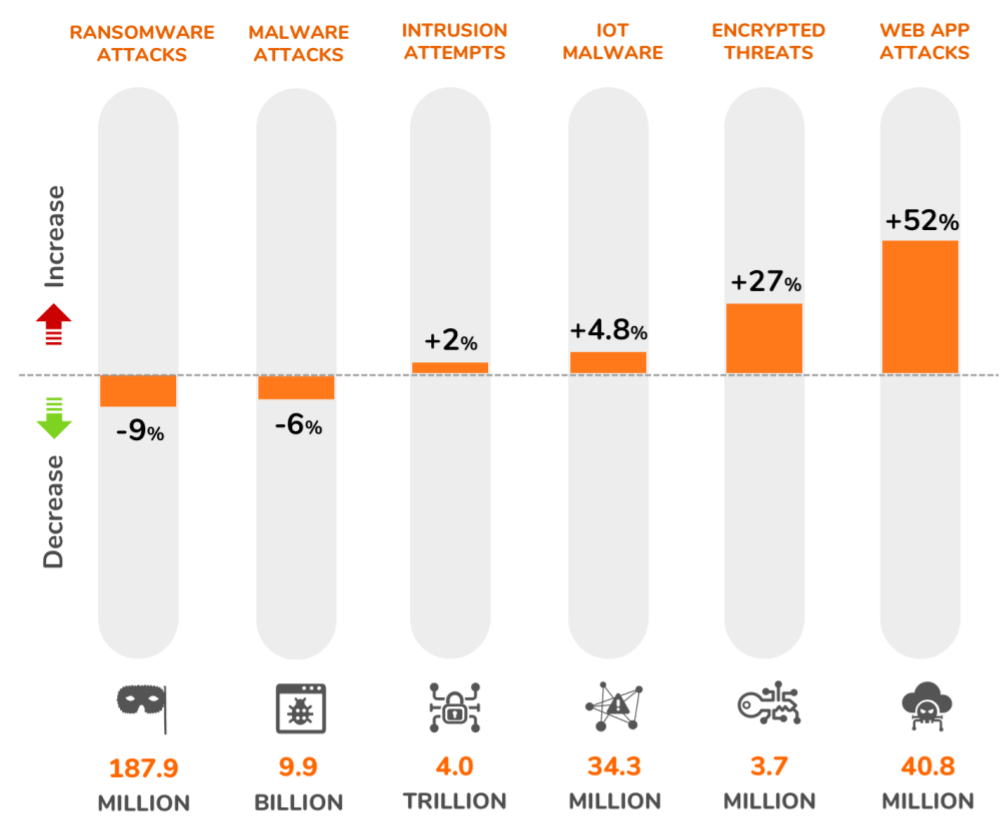
Source: 2020 SonicWall Cyber Threat Report
Phishing declined but persists with personalization
Phishing is still one of the top cyber threats targeting both individuals and organizations. FBI’s 2019 Internet Crime Report noted that the most financially costly phishing complaints involved Business Email Compromise (BEC), amounting to losses of over $1.7 billion in the US alone. Moreover, the Covid-19 pandemic has seen an unprecedented rise in the number of phishing scams, with cyber criminals looking to capitalize on the fear and uncertainty of the crisis.
According to Verizon’s 2020 Data Breach Investigation Report, between 2019 and 2020, phishing was the leading cause of data breaches, accounting for 32% of all attacks. Although email remains the top vector for phishing attacks, cyber criminals are increasingly utilizing other vectors such as SMS, social media, and gaming platforms.
Proofpoint’s 2020 State of the Phish report, which surveyed more than 600 information security professionals across the U.S., Australia, France, Germany, Japan, Spain, and the UK, noted that in 2019, 86% of the participating organizations reported social media attacks, 84% reported SMS phishing (smishing), and 83% reported voice phishing (vishing).
In addition to the increased personalization, phishing tools and techniques are becoming more sophisticated. In 2019, Microsoft reported that attackers randomize domains to exponentially increase the number of phishing URLs, hindering efforts to blacklist such malicious URLs. Moreover, Phishing-as-a-Service (PhaaS) platforms offered on criminal communities such as the dark web lower the cost-of-entry for budding cyber criminals, making phishing scams more prevalent.
Ransomware attacks are more highly targeted
Morphing from spray-and-pray phishing blasts to highly-targeted spear phishing scams, ransomware attacks are becoming more sophisticated and targeted with software services, health care, and government at the top of the victims list. Cybersecurity Ventures predicts that by the end of 2021, global ransomware damages will cost $20 billion and a business will fall victim to a ransomware attack every 11 seconds.
According to SonicWall’s 2020 Cyber Threat Report, while the ransomware attack volume of 187.9 million decreased by 9% from the previous year, targeted ransomware attacks continue to cripple victims. Moreover, bad actors are pivoting towards targeting state, provincial, and local governments given the sensitive data they possess and the large amount of funds at their disposal.
Cyber criminals also continue to deploy ransomware on IoT devices such as smart TVs, electric scooters, smart speakers, refrigerators, doorbells, and toothbrushes.
Botnet activity continues to surge worldwide
Check Point reported a surge in botnet activity with 28% of all organizations worldwide subject to botnet infections in 2019, likely due to the increasing revenue generated through malspam, malware distribution services, and DDoS attacks. Although popular botnets were initially specialized to perform a single task, Check Point reported that they are becoming more diversified in their operations.
According to Imperva’s Global DDoS Threat Landscape Report, 2019 saw the biggest DDoS attack which peaked at 580 million packets per second (Mpps), however, attacks were generally smaller, shorter, and more persistent. Imperva attributed this to the myriad of available DDoS-for-Hire services which reduce the need for advanced technical skills to perform such attacks.
Furthermore, Imperva reported that DDoS offenders employed multi-vector attacks with different streams of payloads (network packets) to bypass enterprise security mechanisms unequipped for complex filtering.
Encrypted attacks are growing steadily
Cyber criminals increasingly use transport layer security (TLS) and secure sockets layer (SSL) encryption standards to evade traditional security controls, such as firewalls, that are unable to block attacks conducted via HTTPs traffic. In 2019, SonciWall Capture Labs recorded 3.7 million malware attacks sent over TLS/SSL traffic—a 27% year-over-year increase.
The percentage of phishing attacks hosted on HTTPs is also increasing steadily. PhishLabs reported that the number of phishing sites protected with SSL increased by 74 percent in the first quarter of 2020. Furthermore, phishers often mount phishing pages within legitimate sites that use SSL.
Web app attacks doubled in 2019
In 2019, SonicWall Capture Labs threat researchers recorded a 52% year-over-year increase in web app attacks. Although the attack volume was largely flat until May, SonicWall recorded spikes in the final seven months of year which pushed the total web app attack volume past 40 million. The top attacks were SQL injection, directory traversal, cross-site scripting (XSS), broken authentication and session management, cross-site request forgery (CSRF), security misconfigurations, and sensitive data exposure.
Furthermore, according to Verizon’s 2020 Data Breach Investigations Report, 43% of data breaches in 2019 were due to attacks on web applications, more than double the results from 2018.
Cutting-Edge Technologies Pose New Threats
With the continued advancement in technology, the global threat landscape will continue to see more advanced threats.
5G will increase vulnerability to IoT threats
In 2019, SonicWall Capture Labs threat researchers measured a moderate 5% increase in IoT malware with a total attack volume of 34.3 million. Howeever, as 5G networks mature, ultimately realizing a global IOT network with billions of connected devices, there will be an increased vulnerability to large-scale, multi-vector Gen V cyber attacks.
Cryptojacking corresponds with cryptocurrency volatility
In the first half of 2019, SonicWall recorded a spike in cryptojacking with 52.7 million registered attacks, notably corresponding with the surge in bitcoin value. However, the dissolution of Coinhive in March 2019 led to the plunge of cryptojacking attack volume by 78% in the second half of the year. SonicWall noted that the volatile shifts and swings of the cryptocurrency market will continue to impact threat actors’ interest in authoring cryptojacking malware.
Cyber criminals are exploiting AI technologies
Although AI dramatically accelerates the identification of new threats and responses to them, cybercriminals are taking advantage of the technology to probe networks, find vulnerabilities, and develop more evasive malware using techniques such as data poisoning.
In addition to developing more evasive malware, AI-based technology such as deepfake are being used by cybercriminals to execute far more sophisticated phishing scams. For example, fraudsters used deepfake to impersonate the voice of a U.K.-based energy firm, retrieving a fraudulent transfer of €220,000 ($243,000).
Drone-enabled network attacks are highly probable
As highlighted in Booz Allen’s 2020 Cybersecurity Threat Trends Outlook report, although drone-enabled network attacks have remained in the realm of controlled research environments, when Bluetooth code execution vulnerabilities like BleedingBit and BlueBorne are disclosed, companies will have to consider drones as a potential vector of exploitation. Although drone-enabled network attacks are unable to rival the scale of traditional remote network attacks due to distance constraints, the threat remains real.
Cloud infrastructures are prone to vulnerabilities
Check Point’s 2020 Cyber Security Report noted a record number of cloud-based data breaches in 2019. Although misconfiguration and mismanagement of cloud resources are the main cause of cloud attacks, Check Point reported an increasing number of attacks aimed directly at cloud service providers.
Furthermore, Check Point highlighted that cloud infrastructure is prone to vulnerabilities which could allow unauthorized attackers to bypass authentication, gain access to a company’s web-based admin interface, and run arbitrary commands as root.
Summing Up
- Cyber crimes will cost the global economy $6 trillion annually by 2021.
- Phishing was the leading cause of data breaches in 2019 at 32%.
- By 2021, global ransomware damages will cost $20 billion.
- In 2019, 28% of all organizations worldwide were attacked by botnets.
- Malware attacks sent over TLS/SSL traffic increased by 27.3% in 2019.
- Web app attacks doubled in 2019—a 52% year-over-year increase.
- Cutting-edge technologies will lead to more advanced cyber threats.